IP Filters or firewalls play a very important role in enhancing the security and performance of networks. When a network packet arrives at a filter, the filter decides whether to let the packet through or not based upon a set of rules (commonly called an access list). Two problems have been identified with packet filters
The Wits Firewall Project, one of the research projects of the Programme for Highly Dependable System, is examining a number of different aspects of firewalling to see how these problems can be addressed. Based on a novel representation of the firewall rules, preliminary experimental results have shown significant potential for not only overcoming these problems, but creating more flexible, powerful and efficient firewalls. We currently have four academic staff, two MSc and four honours students working on different aspects of this project.
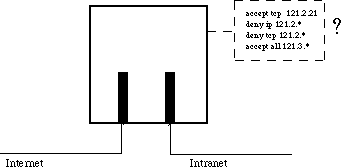
The diagram below is a simplified view of what a firewall or filter does.
 |
A packet arrives from the internet. The firewall examines the IP packet header and consults its rule list. The rule list is examined in order for a rule that matches the header. The first rule that matches is applied and the packet is accepted or rejected depending on what the rule says. Similarly, packets leaving the internet are also examined to see whether they should be passed through or not. |
This is an example of an IP filter because only the IP header (actually sometimes also part of the TCP or UDP header) are examined. There are more sophisticated (and expensive!) firewalls that use information in the higher level protocols to decide what to do.
The new technique looks ideal for flexible hardware implementation. Raymond Sinnappan and Scott Hazelhurst are proposing using field programmable gate arrays (FPGAs) for this. FPGAs have the advantage that they can be reprogrammed, which is ideal for firewalls since we may need to update the rules regularly. Implementing the firewall in hardware not only has the advantage that the lookup can be done far more quickly, but also that a lot of overhead (interrupts and data copying can be avoided). For his MSc research, Raymond has designed an algorithm for convering the access list of a firewall into a form suitable for programming and FPGA, and will be running a series of experiments to develop a performance model for FPGAs.
Analysis of the rules is potentially very useful. A simple protoype tool has been developed that allows a network administrator to view the rules from different perspective, to perform queries on the rules, and to do some limited automatic validation. It is also possible to explore the effects of making changes to the rules.
This tool can be extended in functionality in various ways to allow, for example, graphical analysis, more automatic validation, and conversion from one format into another.
Currently access lists tend to be relatively static. This has several disadvantages since it means that a fixed, global security policy has to be in place at all times. This makes it difficult to cater for different classes of user, as well as for applications which may need varying types of connections when they run. If we have a too strict policy, then certain applications may not be able to run at full functionality; but if we have a too liberal policy then we may open some security holes.
As a simple example, suppose certain types of privileges across the firewall. Allowing those privileges opens up some security holes; not allowing them means that the application will not be able to run. One simple dynamic policy is to allow the firewalls rules to be updates for the period that the application runs. Thus, it is only while the application is running that we open up potential security holes.
PHDS has a virtual redirector project, intended for web applications where there is a need for high availability. A cluster of low-cost servers cooperate among themselves in transparent way to provide service in a scalable way.
Also see our Computational Molecular Biology and Bioinformatics pages.